13. Network Security Management
13.1 Protect networks and facilities
13.1 Protect networks and facilities
The network security controls of Scandiatransplant can be described very easily as only ssl and ssh (port 443 and 80 respectively) are allowed for sensitive data communication; cf. Cryptography Policy Management for details.
All other ports are denied by use of firewalls as described in section 9.1.2 of Control access to networks and network services.
Logging is done partly by Region Midt and the servers running the systems of Scandiatransplant. Inspection is done manually as well as automatically by fail2ban, which subsequently alerts ISPs when heavy or unauthorized attempts are detected. Also firewall openings for ssh are inspected automatically to detect allowed ip’s which hasn’t been used for more than 3 months; e.g. temporarily opened from remote places.
The network service providers are controlled regularly by e.g. database-connection attempts from clients on networks outside of that of the servers. I.e. that the security setup agreed upon in the Service Level Agreement is actually effectured.
The segregation of the networks holding the 5 servers are described in the following diagram:
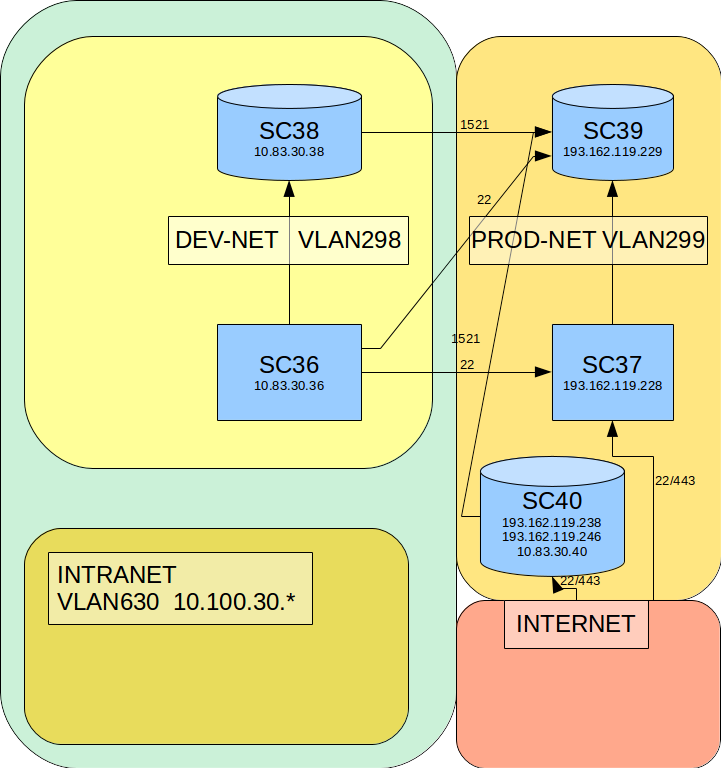
It is a typical DMZ/local-network-setup where the development environment is shielded even more than that of the production-servers, which are available for the users on the internet.
All VLANs are shielded by firewalls administrated by RegionMidt with port-openings specified in the above diagram.

